| keylogger comparison | Anykeylogger | refog keylogger | Revealer keylogger | Elite Keylogger  | All In One keylogger | Ardamax keylogger |
| Price | $29.95 | $69.95 | $39.99 | $79.00 | $69.95 | $44.95 |
| Download Trial | Download | Download | Download | Download | Download | Download |
| OS support | Anykeylogger Windows | Refog personal | Revealer keylogger | Elite Keylogger | All In One keylogger | Ardamax keylogger |
| windows 8 | √ | √ | √ | √ | √ | √ |
| windows 7 | √ | √ | √ | √ | √ | √ |
| Windows Vista | √ | √ | √ | √ | √ | √ |
| Windows XP | √ | √ | √ | √ | √ | √ |
| Windows Server 2003 | √ | √ | √ | √ | ||
| Windows 2000 | √ | √ | √ | √ | ||
| Security | ||||||
| Password protection | √ | √ | √ | √ | √ | √ |
| Accessed by keyword | √ | √ | √ | √ | ||
| Accessed by hotkey | √ | √ | √ | √ | √ | |
| Hidden in Task Manager | √ | √ | √ | √ | √ | √ |
| Hidden starup entries | √ | √ | √ | √ | √ | √ |
| Monitoring | ||||||
| System logon(password) | √ | |||||
| keystrokes | √ | √ | √ | √ | √ | √ |
| screenshots | √ | √ | √ | √ | √ | √ |
| application | √ | √ | √ | √ | √ | |
| password | √ | √ | √ | √ | √ | √ |
| clipboard | √ | √ | √ | √ | √ | |
| sounds | √ | √ | √ | √ | √ | |
| Online Monitoring | ||||||
| hotmail | √ | √ | ||||
| gmail | √ | √ | ||||
| foxmail | √ | √ | ||||
| Yahoo mail | √ | √ | ||||
| Outlook | √ | √ | ||||
| Windows Live Mail | √ | √ | ||||
| Yahoo IM | √ | √ | √ | √ | √ | √ |
| AIM chats | √ | √ | √ | √ | √ | √ |
| Skype chats | √ | |||||
| ICQ chats | √ | √ | √ | √ | √ | |
| websites | √ | √ | √ | √ | ||
| Control | ||||||
| block website | √ | √ | ||||
| block application | √ | √ | ||||
| time control | √ | |||||
| send logs via email | √ | √ | √ | √ | √ | √ |
| Other | ||||||
| Reaction to a specific keyword | √ | √ | ||||
| size | 3.85 MB | 1.77 MB | 1.35 MB | 8 MB | 4.4 MB | 1.6 MB |
| Review | Anykeylogger Windows | Refog personal | Revealer keylogger | Elite Keylogger | All In One keylogger | Ardamax keylogger |
| This type of keylogger is easy to install and use. Its rich functions leave me a good impression.It's not only a keylogger that can be used to record computer activities, but also a parental control tool that can be used to control and manage chidlren's Internet use.And I like its main interface,straightforward and user-friendly. | It flexibly allows you to configure multiple alerts on harmful or offensive keystrokes sent or received on target computer. You can set alarms, and get notified instantly with real-time alerts if a pre-defined event happens on their PC.But it lacks some features if you want to take it as a parental control tool. |
This keylogger is very very simple. If you just want to record keystrokes and screenshots, you can choose it. | It can run on both 32-bit and 64-bit versions of Windows 7, Vista and XP. Unfortunately, the rest of the operating systems are not supported.Its main interface is nice and functions can basically meet users' need of a keylogger.Its price is the highest among all the six keyloggers.It will be better if it can record both side of chats | It has comprehensive functions as a keylogger program, and it works well in recording keystrokes and capturing screenshots, etc.But its delivery feature sometimes fails to work, and for me its price is a little bit high. | It can do most things of that is supposed to be done by a keylogger, while it fails to log email.Other functions works well. | |
| Summary:If you just need a keylogger that can be used to record strokes and screenshots, you can use Revealer Keylogger or Ardamax Keylogger.If you need a keylogger to help you do more things, such as parental control, you'd better choose the other keyloggers, for they have more functions.Judging from price,function, and performance,I think Anykeylogger and Refog Keylogger are better choices. | ||||||
Tuesday, December 24, 2013
Top Keyloggers Compare--Choose Best Keylogger for Windows
Sunday, December 8, 2013
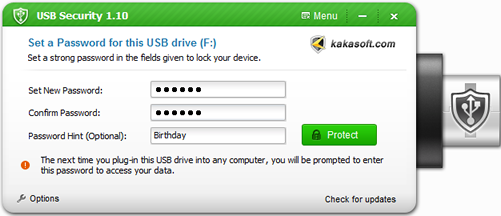
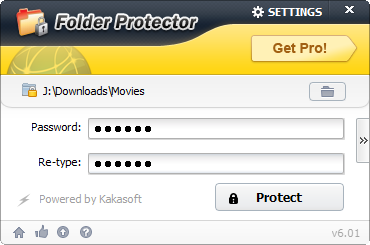
How to completely protect your USB?
Part one: Protect your USB from being accessed
Part two: Protect individual file or folder in USB
Conclusion:
| http://www.wikihow.com/Completely-Protect-Your-USB |
Tuesday, November 26, 2013
Identity Theft and Solutions
You may have heard the news about identity theft happened or happening in our daily life. Now identity theft will appear in many different ways and new methods of information theft will be soon created by those who are living for stealing others’ personal data and information. People who suffered from identity theft must know and understand the different ways of information theft. You should understand how it occurs before you take measures to fight against this crime.
Folder protector donwload link: http://download.cnet.com/Folder-Protector/3000-2092_4-10829601.html?tag=mncol;2
Friday, May 17, 2013
Take Right Actions to Avoid Data Leakage
It’s acknowledged that the biggest problem faced with the USB Flash Drive security of data and the protection from infected viruses and malware which will corrupt the machines that are connected to it or when data are shared. Since the USB flash drive is widely utilized as a powerful storage device, people like to save their documents and information in it and take them anywhere. What if your USB flash drive loses?
As for security, these also act as one of the biggest threat to any organization, as these are so handy that the important and secured data can be easily taken away with no efforts and the company will pay higher price than imagine. So it is prohibited in many corporations to carry a password protect usb drive away.
The solution for this is now available with features like antivirus software, password protection, encryption.
For antivirus software, it will help to ensure that your flash drive won’t be infected by virus. As for password protection and encryption, it can also be helpful to have a password Flash drive. When you are on your home PC, password protection and encryption will help you protect your data in USB drive from other users’ access. Of course, if the data in your USB dive is not only for you yourself, if you want to share the content of you USB drive to others, you can choose a type of flash drive copy protection software which has a function of configuration of access permission, then you can assign access right for different people.
The best secure USB flash drives should adopt the newest government and corporate grade encryption standards, and it should be more than sufficient to protect your data. Its practicality and convenience should meet the requirement of security of both normal users and corporate users. Choose a USB flash drive with proper usb encryption complexity that's comfortable for you.
Apart from utilizing extra protection USB drive, you firstly should use it correctly. Some just take away the USB without properly doing the 'safely remove device' procedure. This sometimes results in loss of data as the data gets corrupted and is lost in this procedure. It is highly recommended that not to try such things if your data is really important.